NIST SP 800-37 (RMF)
NIST SP 800-37 (RMF)
- "The Risk Management Framework (RMF) provides a process that integrates security, privacy, and cyber supply chain risk management activities into the system development life cycle."[1]
- The RMF is intended for use in the US government's authorization to operate process, as compared to the CSF, which is intended for use across industries with fewer administration requirements.
- The RMF is a rigorous, prescriptive framework, which uses risk as the primary motivator in selecting security controls to implement.
- It uses a high-watermark standard of system impact to determine which baseline of controls to select and implement
- The RMF is a 7-step continuous cycle to understand and provide a uniform approach to securing information systems. Below is each step and its associated documentation, per NIST.
- Prepare
- SP 800-18 Rev. 1, Guide for Developing Security Plans for Federal Information Systems | CSRC
- SP 800-30 Rev. 1, Guide for Conducting Risk Assessments | CSRC
- SP 800-39, Managing Information Security Risk: Organization, Mission, and Information System View | CSRC
- SP 800-160 Vol. 1 Rev. 1, Engineering Trustworthy Secure Systems | CSRC
- IR 8062, An Introduction to Privacy Engineering and Risk Management in Federal Systems | CSRC
- Categorize System
- Select Controls
- Implement Controls
- Various publications described in SP 800-53 providing guidance on implementation of controls
- Assess Controls
- Authorize System
- Monitor Controls
- SP 800-37 Rev. 2, Risk Management Framework for Information Systems and Organizations: A System Life Cycle Approach for Security and Privacy | CSRC
- 1. SP 800-53A Rev. 5, Assessing Security and Privacy Controls in Information Systems and Organizations | CSRC
- SP 800-137, Information Security Continuous Monitoring (ISCM) for Federal Information Systems and Organizations | CSRC
- Prepare
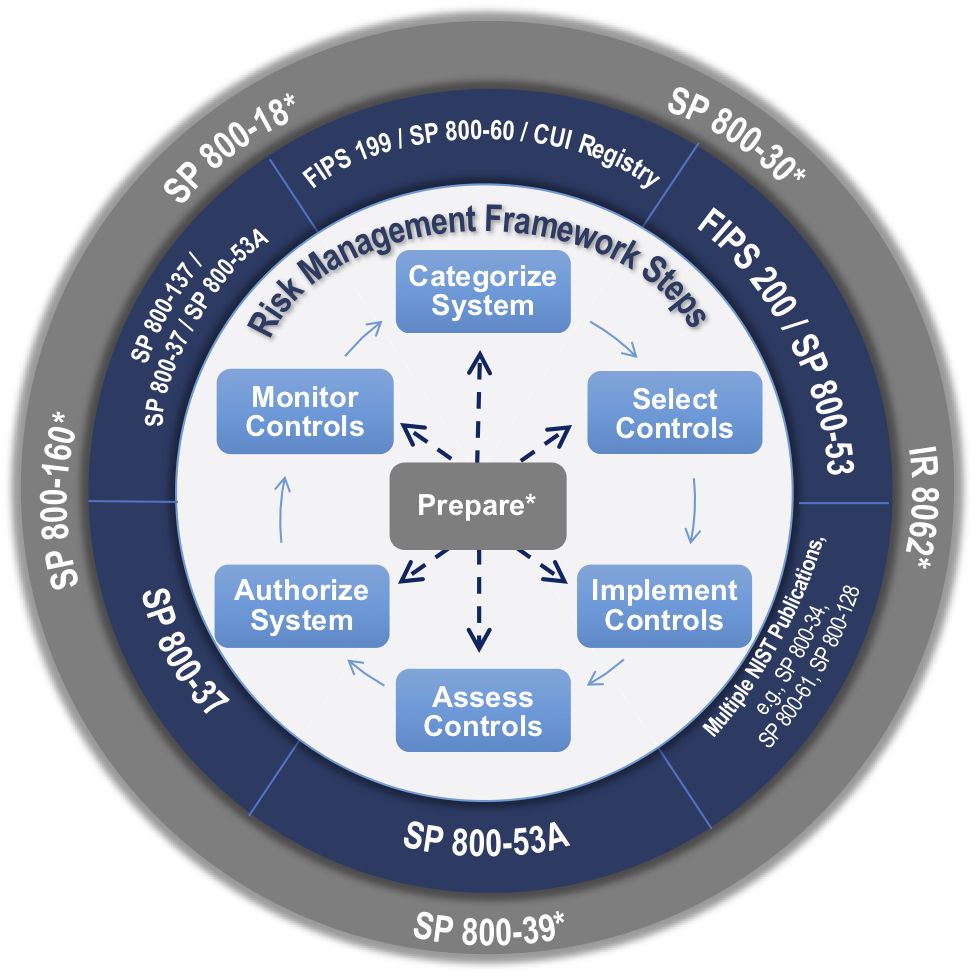
NIST's RMF wheel highlighting key documentation.[2]
RMF map created by Aron Lange:[3]
Critical Documents in the RMF Process
These documents are required for FISMA compliance, under the step in which they are created.[4]
- 3. Select Controls and 4. Implement Controls
- SSP: Security Plan
- Defines what should be implemented
- This is a living document; it should accurately describe the controls protecting the system
- SSP: Security Plan
- 5. Assess Controls
- SAP: Assessment Plan
- Defines how to test implementations
- SAR: Assessment Report
- Documents what was found
- POA&M: Plan of Action and Milestone
- Tracks what needs to be fixed
- SAP: Assessment Plan
Each document feeds into the next, and missing documents can can lead to process failures or not being being granted authorization to operate.
flowchart TD A["SSP: System Security Plan Defines control implementation"] ==> B[SAP: System Assessment Plan How to assess implementation] B ==> C[SAR: System Assessment Report Describes all assessment findings] C ==> D[POA&M: Plan of Action and Milestones Track what needs to be fixed] C -->|SAR findings reference SSP control numbers| A D -->|POA&M items are linked to assessment findings| C D -->|SSP updated to reflect closed items in POA&M| A B -->|SAP tests are mapped to controls defined in SSP| A
RMF Step Guide
- Prepare:[5] Setup the organization for success
- Identify systems and stakeholders in the business and assign role for executing the RMF
- Conduct a risk assessment[6] and get a baseline of current risk and security practices
- Categorize: Identifying potential impact
- FIPS 199 and FIPS 200 are used to identify the potential security and privacy impact of a system breach to organizations and individuals
- Ratings of Low, Moderate, and High are applied to the three pillars of the CIA Triad; confidentiality, integrity, availability
- A Low rating means that a loss of one of the pillars would have a limited adverse effect on victim organizations or individuals
- A Moderate rating means a serious effect
- A High rating is severe or catastrophic effect
- This is a high watermark standard, meaning that the highest rating for the system in the triad applies to the entire system
- FIPS 199 provides more examples, but a system with low confidentiality, moderate integrity, and high availability ratings would be required to use the high impact baseline
- Over-speccing can lead to wasted resources, underspeccing can leave critical systems vulnerable
- Ratings of Low, Moderate, and High are applied to the three pillars of the CIA Triad; confidentiality, integrity, availability
- NIST SP 800-60 provides guidelines on the impact you should assign to certain systems
- The NIST CSF
- FIPS 199 and FIPS 200 are used to identify the potential security and privacy impact of a system breach to organizations and individuals
- Select: Select controls to implement from NIST 800-53
- The 800-53 is basically a big dictionary with hundreds of controls
- Start with the baseline for your system's impact in 800-53B
- Tailor the controls to your organization
- The outcome of this step is the SSP (System Security Plan), and instructions on how to create one are found in the NIST SP 800-18
- This is the book/plan for the documentation of your system
- Network diagram, who owns the system, what kind of data is stored, etc.
- All the controls to secure the systems and how they are implemented
- May be more or less complicated, depending on the size of the organization
- Gerald specifically mentions the NIST SP 800-15, but it was withdrawn in September of the year he published his video
- This is the book/plan for the documentation of your system
- The 800-53 is basically a big dictionary with hundreds of controls
- Implement: Implement the controls (the lion's-share of the work)
- If you have any challenges implementing controls, NIST has implementation guides for most systems
- NIST offers tons of instructions and things you can do
- If you have any challenges implementing controls, NIST has implementation guides for most systems
- Assess: Bring in an independent auditor to inspect your controls
- The SSP is used to create the SAP (System Assessment Plan) with the help of the 800-53A
- The plan should include information like:
- Duration of site visits
- Who need to be interviewed
- What evidence is required
- Which controls will be tested
- When the report will be delivered
- The auditor should have a solid understanding of the controls you are investigating and be able to provide color and ask questions beyond the stated control in the 800-53R5
- The 800-53 can be quite technical, so making it understandable to regular humans is key.
- The plan should include information like:
- The SAR (System Assessment Report) and POA&M (Plan of Action and Milestones) are created as part of this step
- The SAR includes all information for the controls assessed, including the auditor's findings
- The POA&M maps those findings to actionable items and is prepared by the system owner.
- For FISMA or any kind of certification, organizations will need an external, independent auditor to conduct the assessment
- The SSP is used to create the SAP (System Assessment Plan) with the help of the 800-53A
- Authorize: Authorize the system
- Basically just a memo from the person responsible authorizing the system to operate
- Usually just a page or so with their signature
- What's missing in this (as of 2021) is a risk assessment
- Use NIST SP 800-30 to asses risk
- Residual risk for controls not implemented, etc.
- Use NIST SP 800-30 to asses risk
- This grants an Authorization to Operate for 1-3 years, depending on the requirements
- Basically just a memo from the person responsible authorizing the system to operate
- Monitor: Monitor the controls
- Systems are monitored and brought re-audited at regular intervals
- The system owners continue conducting assessments, risk treatment, and work on the implementing the POA&M
- Often the audits are often scheduled to be tested in a kind of sequence to prevent infrequent massive effort
Resources
Official
- NIST Risk Management Framework | CSRC
- dhs.gov/sites/default/files/2023-08/23_0803_cpo_ security-authorization-process-guide.pdf
- This is the DHS "System Security Authorization Process Guide"
- 32 pages (66 with appendices) that maps the RMF to their ATO (authorization to operate) process.
Supplemental
Articles
NIST Risk Management Framework - by Aron Lange- Super short and has a great graphic which details every step and task of the RMF
- Original link down; updated link to LinkedIn post here, which has additional resources and the graphic but lacks the article: 💥Here are some of the top free resources that will help you to break into GRC and information security. - Aron Lange
Videos
- Dr. Gerald Auger[7]
- Definitive Guide to RMF (Actionable plan for FISMA Compliance) - YouTube
- 15 minute long video
- Older, includes references to documents that have been withdrawn and doesn't include the "Prepare" phase
- NIST RMF FULLY EXPLAINED (IN PLAIN ENGLISH) - YouTube
- 1h12m video long
- I love and hate Gerry Auger videos; his content is great and helpful, but his style meanders and can be very distracting
- Definitive Guide to RMF (Actionable plan for FISMA Compliance) - YouTube
Risk Management Framework (RMF) Overview - FISMA Implementation Project | CSRC ↩︎
Here are some of the top free resources that will help you to break into GRC and information security. - Aron Lange ↩︎
dhs.gov/sites/default/files/2023-08/23_0803_cpo_ security-authorization-process-guide.pdf ↩︎
Not discussed in Gerald's video, but detailed here for reference. ↩︎
SP 800-30 Rev. 1, Guide for Conducting Risk Assessments | CSRC ↩︎
oh-zher ↩︎